The ever-increasing use of low-power wireless sensor technology for sensing and monitoring applications, including use cases within critical infrastructure, identifies a need to make this technology robust against cyber-attacks. Within SWAN, we have adopted LoRaWAN, a proprietary low-power wide area technology developed for the Internet of Things (IoT), as a candidate technology for detailed evaluation given the increasing prevalence within remote telemetry applications. SWAN is addressing radio frequency (RF) based cyber-attack detection and mitigation, rather than network orientated intrusion.
By developing methods of RF fingerprinting that can be applied to LoRa, the SWAN research team hopes to be able to create unique identifiers, like biological fingerprints, that will enable networks to detect potential intrusions.
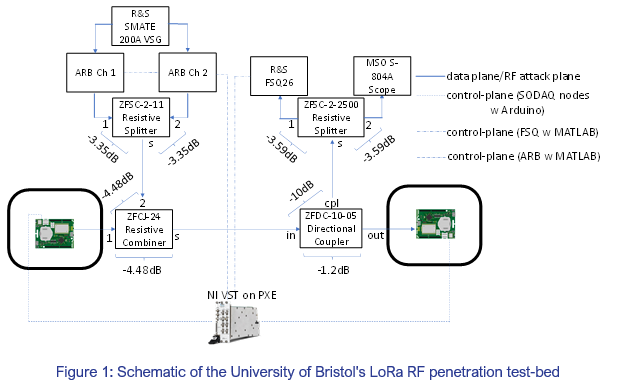
As shared in the Winter 2021 SWAN newsletter, SWAN’s postdoctoral researchers have developed an RF penetration test-bed (pen-test) to facilitate the injection of jamming waveforms. They have now progressed to using the test-bed for the extraction live over-the-air (OTA) waveforms for RF fingerprinting, with LoRa as a first candidate air interface technology. The set-up is illustrated in Figure 1.
As shown in Figure 1, waveform monitoring and penetration injection testing is implemented by means of cabled RF couplers, making use of extensive test and measurement equipment in the Communication Systems & Networks lab. Figure 2 shows a photo of the test-bed.
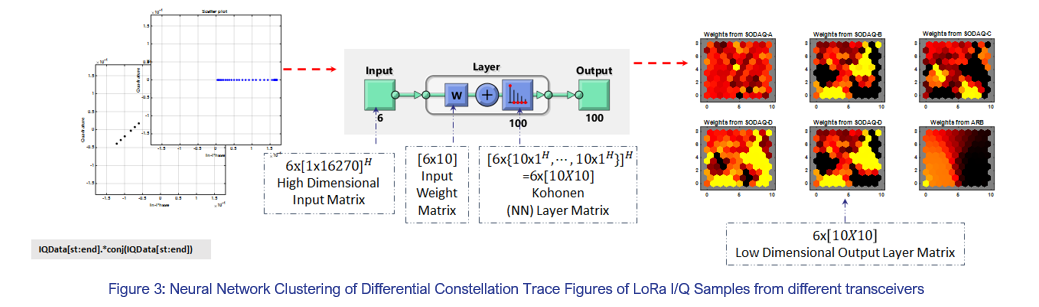
SWAN’s postdoctoral researchers are developing a two-pronged methodology for RF fingerprinting of the start-up chirps from a LoRa modem. Firstly, a self-organising feature map (SOFM) is trained using unsupervised competitive learning of neural network (NN) clusters to produce two-dimensional (2D) discretised representations of the input space. The procedure is illustrated in Figure 3. As shown in Figure 3, the input space consists of the differential constellation trace of LoRa I/Q samples. These I/Q samples are extracted from LoRa RF transmissions form different LoRa transceiver modules (RN2483 from Microchip); as well as a baseband LoRa waveform that is generated in MATLAB, then up converted and transmitted using a vector signal generator (VSG).
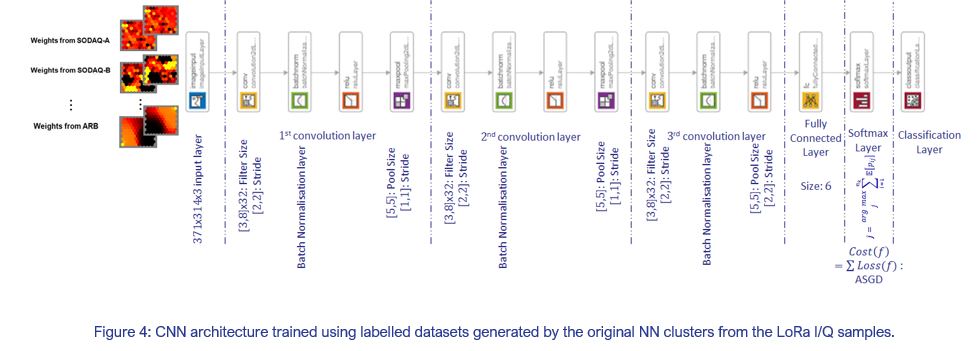
Secondly, an optimised deep convolutional neural network (CNN) architecture with batch normalisation at every convolutional layer is proposed. The CNN is trained using labelled datasets compiled from the 2D SOFMs from multiple training epochs of the original NN clusters. The proposed architecture, depicted in Figure 4, is expected to be invariant medium access control (MAC) ID spoofing. In other words, it learns only physical (PHY) layer features due to the differential constellation trace of LoRa I/Qs without learning the MAC features. Our current work demonstrates cent-percent accuracy.
Further research for increasing the robustness of this approach will incorporate adding additive white Gaussian noise (AWGN) and channel impairments for the emulation of OTA transmission.