When our team kicked off the SWAN (Secure Wireless Agile Networks) Prosperity Partnership in February 2020, we eagerly started planning a series of training seminars for our research team aimed at filling the initial gaps in our knowledge base.
Little did we know that we would soon all be working from home as a part of a national lockdown resulting from the COVID-19 global pandemic.
In spite of the physical distance and the new working environment, we were able to host a series of highly valuable internal training webinars, expertly delivered by colleagues in two of our partner institutions, Toshiba Europe Ltd and Roke Manor Research. We wanted to share our experience of delving into these first few training sessions, highlighting how this partnership has allowed us to push on with this important research remotely while navigating the pitfalls of Covid-19.
The first steps for the SWAN programme
The SWAN programme aims to identify vulnerabilities in RF interfaces, an attack surface that has so far attracted little research attention in spite of the increasing risk to various critical networks. Once these vulnerabilities have been identified, the programme will focus on developing techniques that can be used to detect and mitigate against the effects of cyber-attacks on RF interfaces.
The research team at the University of Bristol benefits from leading expertise in physical layer wireless research, RF technologies, and Dynamic Spectrum Access (DSA). However, the team has less experience in cyber security and threat assessment, two areas in which several of our colleagues from Toshiba and Roke excel.
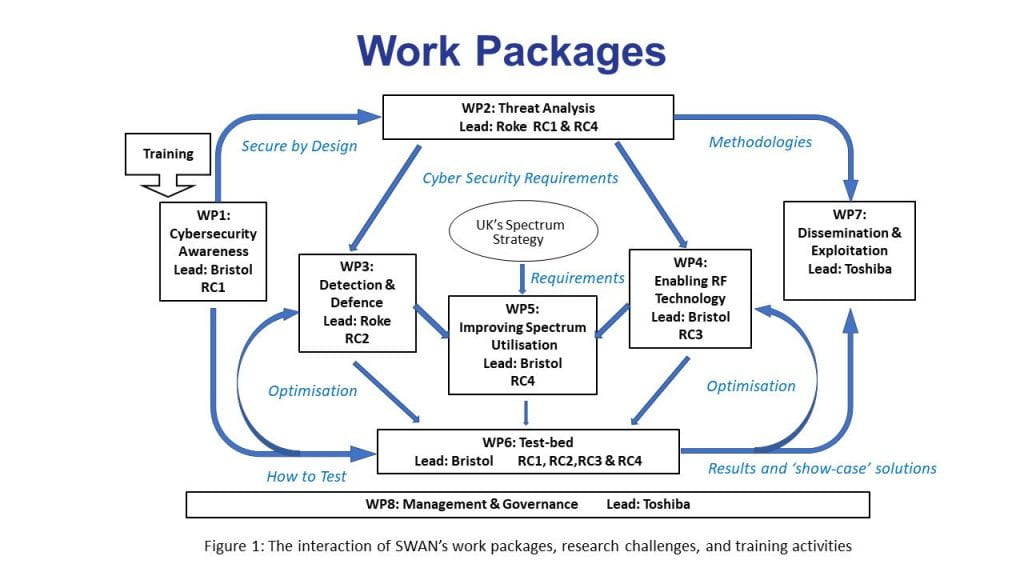
Through the delivery of a number of training webinars, feeding in to Work Package 1 of the programme (see Figure 1), the SWAN team have been able to strengthen their knowledge, building on the expertise of our industrial partners to put them in as strong a position as possible before tackling the SWAN Research Challenges in earnest.
Intro to Cyber Security – Theo Spyridopoulos (Toshiba Europe Ltd)
 Kicking off the initial training series, Theo Spyridopoulos, Senior Research Engineer at the Toshiba Europe Bristol Research and Innovation Laboratory (BRIL), gave a preliminary grounding for the team in the essentials of cyber security.
Kicking off the initial training series, Theo Spyridopoulos, Senior Research Engineer at the Toshiba Europe Bristol Research and Innovation Laboratory (BRIL), gave a preliminary grounding for the team in the essentials of cyber security.
Theo’s background in cyber security of Industrial Control Systems from both an academic research perspective, during his Senior Lectureship at the University of the West of England, and through industrial experience in aerospace, meant he was ideally placed to show the importance of cyber security in industrial settings.
In this webinar, Theo gave an overview of the conventional technical, managerial and operational cyber security controls applied in IT systems and the implications that arise from their use in Operational Technology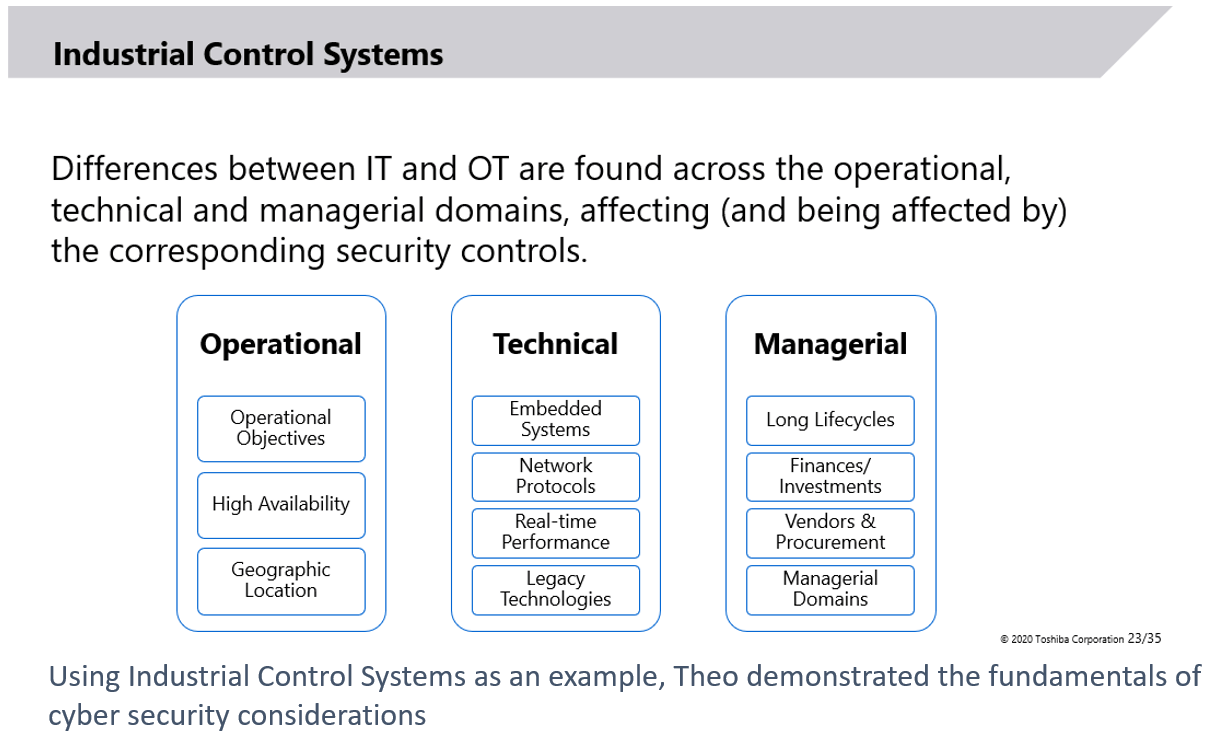 systems. Traditionally, Industrial Control Systems were isolated systems designed with no security in mind; however, their connection to external networks such as the Internet along with the introduction of COTS technologies to improve their performance has rendered them vulnerable to cyber threats. Using these types of systems as an example, Theo demonstrated the fundamentals of cyber security considerations to the SWAN team.
systems. Traditionally, Industrial Control Systems were isolated systems designed with no security in mind; however, their connection to external networks such as the Internet along with the introduction of COTS technologies to improve their performance has rendered them vulnerable to cyber threats. Using these types of systems as an example, Theo demonstrated the fundamentals of cyber security considerations to the SWAN team.
With this grounding in the basics of cyber security from an industrial systems perspective, the team were ready to look a little deeper into methods of threat assessment and models for analysing and predicting system vulnerabilities.
An Introduction to Risk and Threat Modelling – Alex Collins and Professor Mark West (Roke)
 For the next stage in our training webinar series, Alex Collins and Professor Mark West from Roke took the research team on a tour of risk and threat modelling, drawing on an extension of the Microsoft STRIDE model to include open RF attack surfaces as an example.
For the next stage in our training webinar series, Alex Collins and Professor Mark West from Roke took the research team on a tour of risk and threat modelling, drawing on an extension of the Microsoft STRIDE model to include open RF attack surfaces as an example.
Alex Collins is the Head of Profession in Cyber & Networks and is a lead solution architect in cyber and lawful interception domains. He acts as the University Liaison for Roke with the Cyber Security Academy at Southampton University and serves on the Industrial Advisory Board for Oxford University’s Cyber Centre for Doctoral Training.
Professor Mark West is the Head of Profession in Information Assurance and Human Science. Mark is an expert in cyber and information security, a board member of Southampton CSA and led recent work to secure automotive and other transport platforms. He is an expert in Internet standardisation as well as EU and UK/US collaborative research programmes.
 After outlining the key methods of assessing and managing risk, Alex and Mark illustrated how threat modelling can be used to improve the security of systems. In particular, Alex and Mark highlighted the potency of methods of gamification in threat modelling, sharing with the team their prototype deck of RF STRIDE cards to assist with the assessment of potential threats to a system.
After outlining the key methods of assessing and managing risk, Alex and Mark illustrated how threat modelling can be used to improve the security of systems. In particular, Alex and Mark highlighted the potency of methods of gamification in threat modelling, sharing with the team their prototype deck of RF STRIDE cards to assist with the assessment of potential threats to a system.
This approach with the STRIDE cards would go on to play a key role in the next stage of the SWAN research programme, a white paper outlining possible threats via the RF interface to various wireless systems, including Long-Term Evolution (LTE) 4G and 5G systems, Internet of Things (IoT) technology, and Wireless Fidelity (WiFi).
Once published, this white paper will be available to view on the SWAN Website.
Equipment demonstration webinars
Alongside the training provided by our industrial partners, the SWAN team have also benefited from a number of equipment demonstration webinars delivered by external collaborators Rohde & Schwarz, Anritsu, Keysight, and Spirent.
These webinars have provided key insights into the types of equipment SWAN will need to build into the test-bed that will form Work Package 6 of the programme (see Figure 1).
Continuing with the SWAN work programme
Going forward, the SWAN team will continue to draw on the expertise of our partners to develop our knowledge base and strengthen our research programme. Further down the line, we will also begin to bring in expertise from outside the consortium to raise awareness of cyber security design considerations in specific wireless systems, such as Internet of Things (IoT).
This will culminate in an internal virtual hackathon in December. Keep an eye on the SWAN website for updates about the hackathon and other upcoming activities.